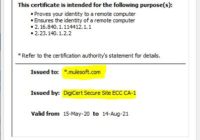
SSL vs TLS: What is the Difference Between SSL and TLS
SSL is widely used since long to achieve security of data communicated over public networks. In OSI seven layer model, SSL sits between the Application layer and the Transport layer, traditionally seen as part of the Presentation layer. SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are two very common words which are often… Read More »