SSL (Secure Socket Layer) is the standard technology used for enabling secure communication between a client and sever to ensure data security & integrity. SSL has evolved with time and several versions have been introduced to deal with any potential vulnerabilities. SSL V2 released in 1995 was the first public version of SSL followed by SSL V3 in 1996 followed by TLS V1.0 in 1999, TLS V1.1 in 2006 and TLS V1.2 in 2008.
For ensuring security of the data being transferred between a client and server, SSL can be implemented either one-way or two-way. In this post, I will briefly explain the difference between One-Way SSL and Two-Way SSL (also known as Mutual SSL).
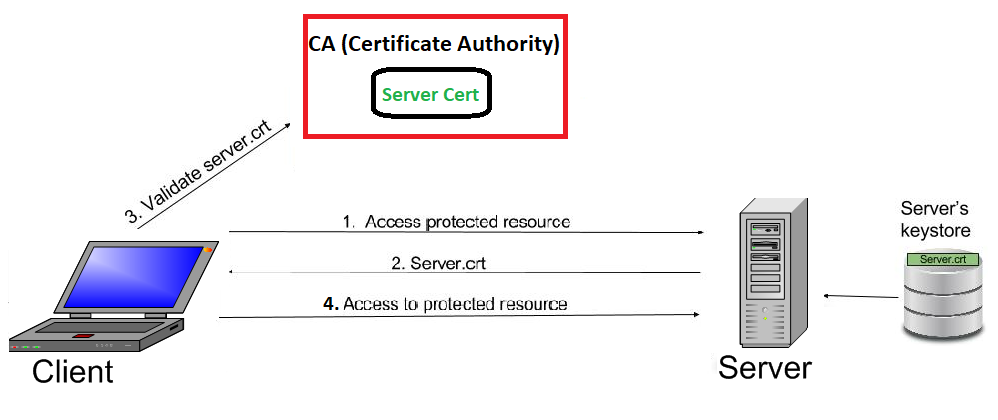
How One-Way SSL Works?
In one way SSL, only client validates the server to ensure that it receives data from the intended server. For implementing one-way SSL, server shares its public certificate with the clients.
Below is the high level description of the steps involved in establishment of connection and transfer of data between a client and server in case of one-way SSL:
1. Client requests for some protected data from the server on HTTPS protocol. This initiates SSL/TLS handshake process.
2. Server returns its public certificate to the client along with server hello message.
3. Client validates/verifies the received certificate. Client verifies the certificate through certification authority (CA) for CA signed certificates.
4. SSL/TLS client sends the random byte string that enables both the client and the server to compute the secret key to be used for encrypting subsequent message data. The random byte string itself is encrypted with the server’s public key.
5. After agreeing on this secret key, client and server communicate further for actual data transfer by encrypting/decrypting data using this key.
Below is the pictorial description explaining how one way ssl works:
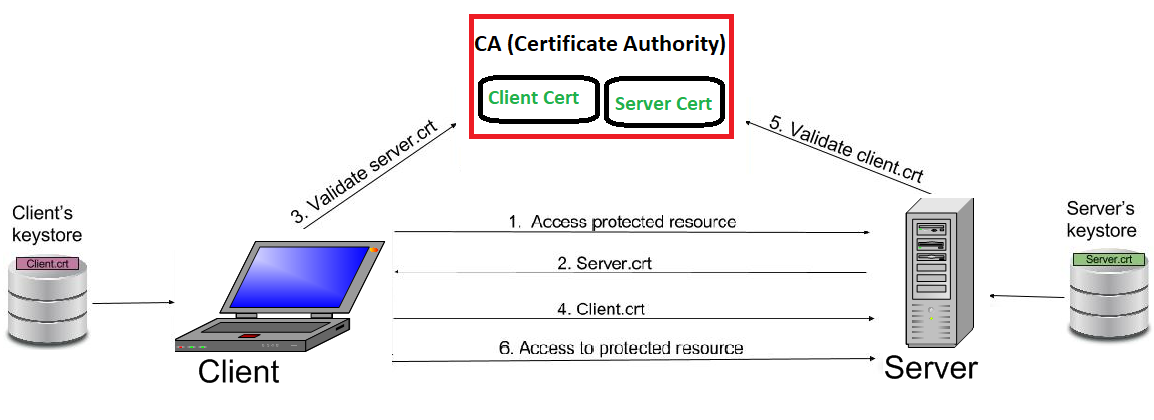
How Two-Way (Mutual) SSL works?
Contrary to one-way SSL; in case of two-way SSL, both client and server authenticate each other to ensure that both parties involved in the communication are trusted. Both parties share their public certificates to each other and then verification/validation is performed based on that.
Below is the high level description of the steps involved in establishment of connection and transfer of data between a client and server in case of two-way SSL:
1.Client requests a protected resource over HTTPS protocol and the SSL/TSL handshake process begins.
2 Server returns its public certificate to the client along with server hello.
3. Client validates/verifies the received certificate. Client verifies the certificate through certification authority (CA) for CA signed certificates.
4. If Server certificate was validated successfully, client will provide its public certificate to the server.
5. Server validates/verifies the received certificate. Server verifies the certificate through certification authority (CA) for CA signed certificates.
6. After completion of handshake process, client and server communicate and transfer data with each other encrypted with the secret keys shared between the two during handshake.
Below image explains the same in pictorial format:
I have also uploaded a video with a detailed explanation of differences between one-way and two-way ssl, how one-way and two-way SSL work and a in-depth explanation of how SSL handshake takes place between client and server for SSL communication.
Watch the video below and also don’t forget to subscribe to TutorialsPedia Youtube channel:
Further Reading:
An overview of SSL Certificate Chaining: How Chain of Trust Works in for SSL/TLS?
How to Generate Self-Signed Certificates Using Java KeyTool
How to Generate Self Signed Certificates, Keys and CSR using OpenSSL

In Two-Way (Mutual) at point no 5, I am confused.
Can you please confirm is it verify /validate by client or server. Ideally it should be validate by the server as client is sending its public certificate.
Is it typo error?
Since it is two-way SSL; both client and server validate each other’s certificates.
Sir,
Could you please explain how to generate certificate for client.
Step 5 seems to be wrong. Isn’t it server who is validating and the random key string generation step seems to be pretty vague. Who generates it?
line 5 is the same as line 3
lne 5 should be server …
Thanks for correcting. It was a mistake. Has been corrected.
Pingback: Istio Multicluster on OpenShift – Red Hat OpenShift Blog
Sir,
I’m a student. I decided TWO-WAY SSL AUTHENTICATION as my final project. I hope to do this using CENTOS and APACHE server. I have already created a web page to do this, but I have some problems with the configuration part. Could you please help me to do this.
Thank you.
If there is no CA Authority How it works. Does Client have both Client as well as Server certificates stored locally.
Pingback: SSL单向与双向认证 | 大专栏
I am using the certificate from Sectigo/Comodo. Now I need to connect to one of our client with two way authentication using php. So anyone please suggest me something I am having any clue how to do the same.
I also don’t know am I using Two Way ssl Certificate or not..
Any Help will be really appreciated.
Pingback: SSH symmetric, asymmetric encryption and hashes – Tefter Webdeveloper.BG
Pingback: One-Way SSL and Two-Way SSL – Tefter Webdeveloper.BG
I am getting this error:14094410:SSL routines:SSL3_READ_BYTES:sslv3 alert handshake failure
Pingback: Https双向验证与Springboot整合测试-人来人往我只认你 | 28RG新闻网
Pingback: Https双向验证与Springboot整合测试-人来人往我只认你 – Programming language
In case of one way ssl, client sends the hello message, not the server as mentioned above
Pingback: SSL Certificate Chain: SSL/TLS Concepts, Root Certificate, Intermediate and Server Certificate and Chain of Trust Explained | TutorialsPedia
Pingback: SSL Certificate: How SSL/TLS Works: SSL/TLS Introduction
Pingback: API Security Best Practices : 8 APIs Security Best Practices